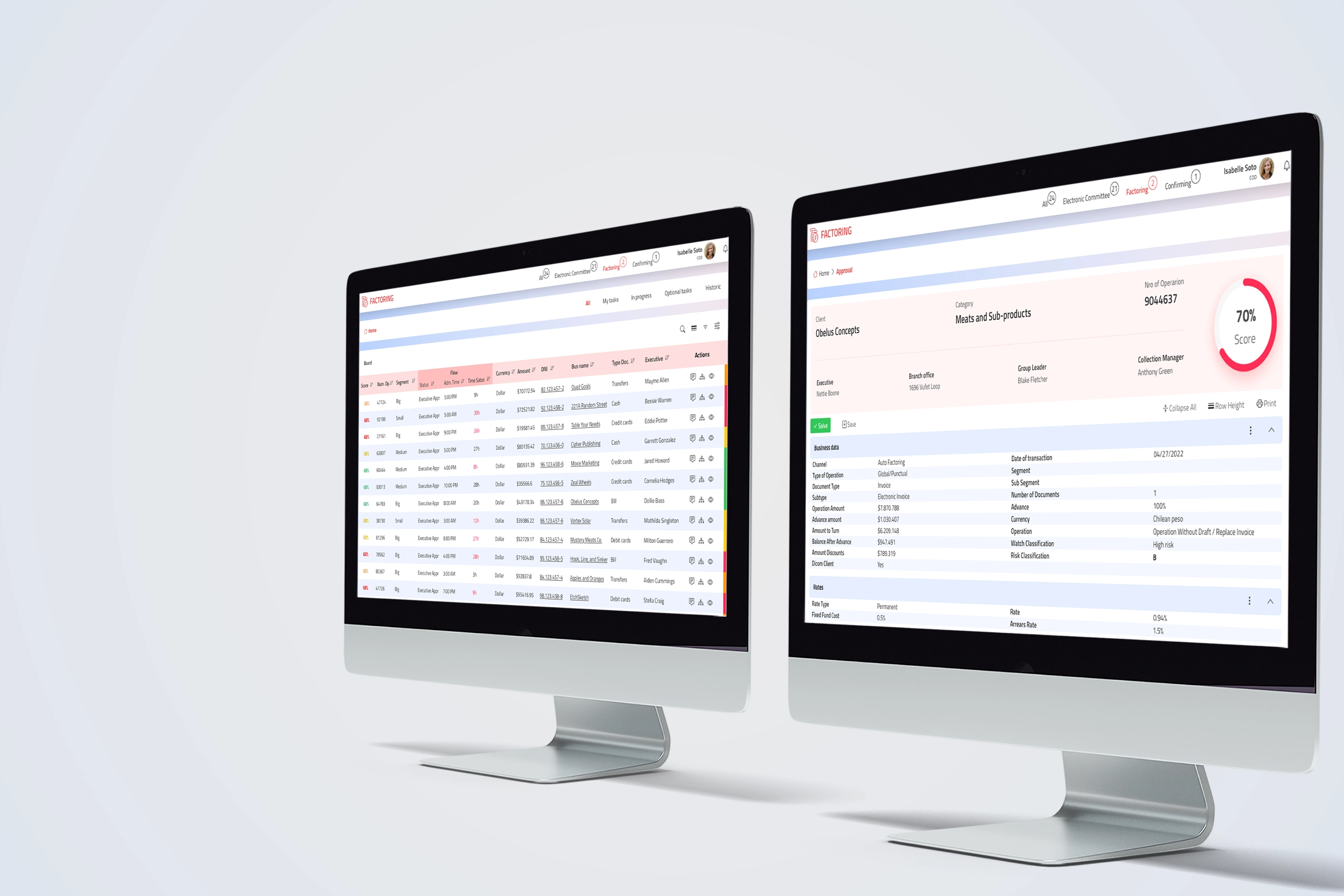
Project Overview
A comprehensive financial security platform designed to transform how businesses manage factoring processes while ensuring maximum data protection. This solution creates a secure, intuitive environment for handling sensitive financial transactions and documents.
The Challenge
Businesses needed a reliable way to manage factoring operations while protecting sensitive financial data from increasingly sophisticated security threats. Traditional solutions created friction between security and usability, often sacrificing one for the other.
Discovery & Research
Security Landscape Analysis
I conducted an extensive analysis of current financial security vulnerabilities and best practices, revealing critical patterns that informed our approach:
- Threat Assessment - Identifying common attack vectors in financial platforms
- Compliance Mapping - Analyzing regulatory requirements across multiple markets
- User Behavior Studies - Understanding how security measures impact user workflows
- Competitive Evaluation - Examining security implementations across the industry
User Research Highlights
In-depth conversations with experts to understand technical requirements and emerging threats. Comprehensive discussions with end-users to identify pain points in current security implementations. Detailed observation of real-world workflows to identify security friction points.
Key Research Insights
- Users frequently bypass security measures they perceive as too cumbersome
- Most security breaches occur through social engineering rather than technical vulnerabilities
- Financial professionals need continuous visibility into security status without disruption
- Trust indicators must be both visible and meaningful within the user interface
User Personas
Rafael Moreno
Financial Operations Manager
Mid-market enterprise • Technical Proficiency: Moderate
Security Behaviors
- Regularly handles sensitive financial documents
- Manages team access to financial systems
- Responsible for compliance reporting
- Balances operational efficiency with security protocols
Pain Points
- Complex security procedures slow down time-sensitive transactions
- Difficulty tracking which team members have access to specific documents
- Frustration with multiple authentication steps throughout the day
- Uncertainty about whether security measures are actually effective
Design Approach
We developed a comprehensive security-focused design approach that balances protection with usability:
- Security-First Architecture: Layered security model that protects data at rest, in transit, and during user interactions
- Progressive Authentication: Contextual security system that adapts authentication requirements based on user behavior and risk
- Trust-Building Interface: Clear security indicators and status visualizations that build user confidence
- Seamless Recovery Mechanisms: Intuitive processes for handling security exceptions without compromising protection
Key Features
Intelligent Risk Detection
Advanced algorithms identify unusual patterns and potential security threats without disrupting legitimate user activities.
Document Vault
Military-grade encryption for sensitive financial documents with granular access controls and comprehensive audit trails.
Compliance Dashboard
Real-time visibility into security status and compliance metrics with actionable notifications for potential issues.
Secure Collaboration
Protected communication channels and document sharing features that maintain security while enabling team collaboration.
Results & Impact
96%
Security compliance across all client organizations
+42%
Increase in security feature adoption compared to industry average
-38%
Reduction in security-related support tickets
Zero
Data breaches during the first year of implementation
This project demonstrated that exceptional security and outstanding user experience are not mutually exclusive. By deeply understanding both security requirements and user workflows, we created a solution that protects sensitive financial data while enabling efficient operations. Future development will focus on expanding AI-powered threat detection capabilities and enhancing cross-platform security synchronization based on ongoing user feedback and emerging security threats.